Глава 14. Configuring VPN Server¶
Содержание
Аннотация
Nowadays, the Internet connection is cheap and available almost everywhere. It is important that the connection is as secure as possible. Virtual Private Network (VPN), is a secure network within a second, insecure network such as the Internet or WLAN. It can be implemented in different ways and serves several purposes. In this chapter, we focus on VPNs to link branch offices via secure wide area networks (WANs).
14.1. Conceptual Overview¶
This section defines some term regarding to VPN and introduces a brief overview of some scenarios.
14.1.1. Terminology¶
- Endpoint
The two «ends» of a tunnel, the source or destination client
- Tap Device
A tap device simulates an Ethernet device (layer 2 packets in the OSI model such as IP packets). A tap device is used for creating a network bridge. It works with Ethernet frames.
- Tun Device
A tun device simulates a point-to-point network (layer 3 packets in the OSI model such as Ethernet frames). A tun device is used with routing and works with IP frames.
- Tunnel
Linking two locations through a primarily public network. From a more technical viewpoint, it is a connection between the client's device and the server's device. Usually a tunnel is encrypted, but it does need to be by definition.
14.1.2. VPN Scenarios¶
Whenever you setup a VPN connection your IP packets are transferred over your secured tunnel. A tunnel can use a so-called tun or tap device. They are virtual network kernel drivers which implement the transmission of ethernet frames or ip frames/packets.
Any userspace program OpenVPN can attach itself to a tun or tap device to receive packets sent by your OS. The program is also able to write packets to the device.
There are many solutions to set up and build a VPN connection. This section focuses on the OpenVPN package. Compared to other VPN software, OpenVPN can be operated in two modes:
- Routed VPN
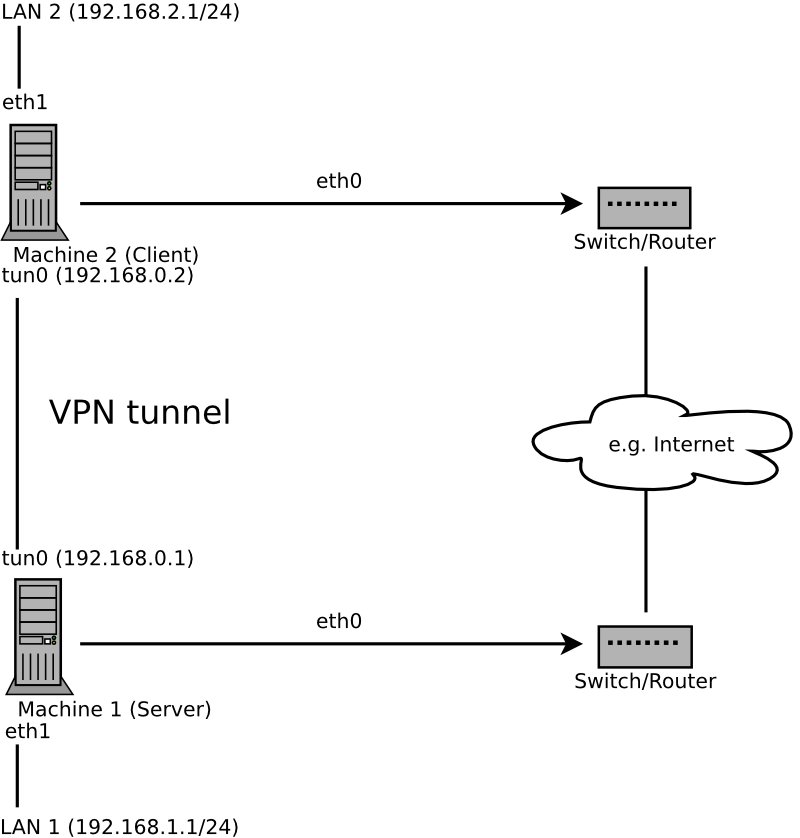
Routing is an easy solution to set up. It is more efficient and scales better than bridged VPN. Furthermore, it allows the user to tune MTU (Maximum Transfer Unit) to raise efficiency. However, in a heterogeneous environment NetBIOS broadcasts do not work if you do not have a Samba server on the gateway. If you need IPv6, each tun drivers on both ends must support this protocol explicitly. This scenario is depicted in Рисунок 14.1, «Routed VPN»
- Bridged VPN
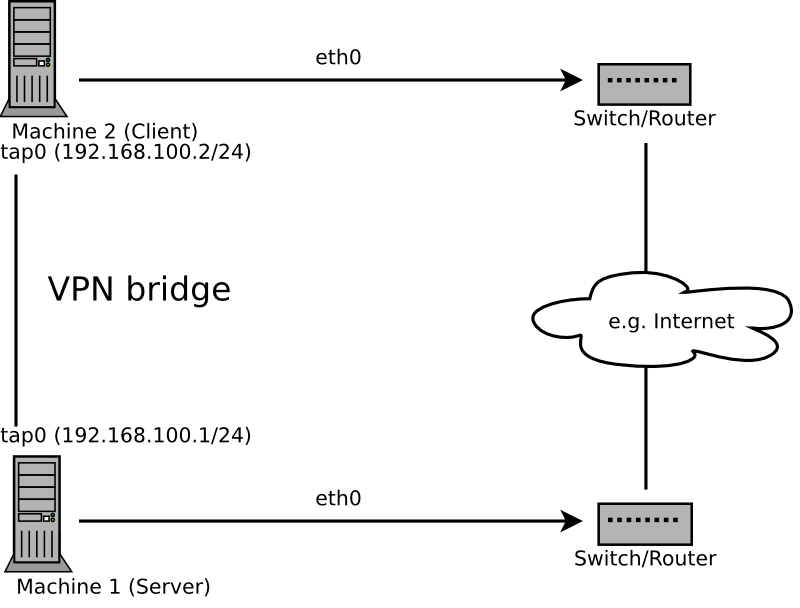
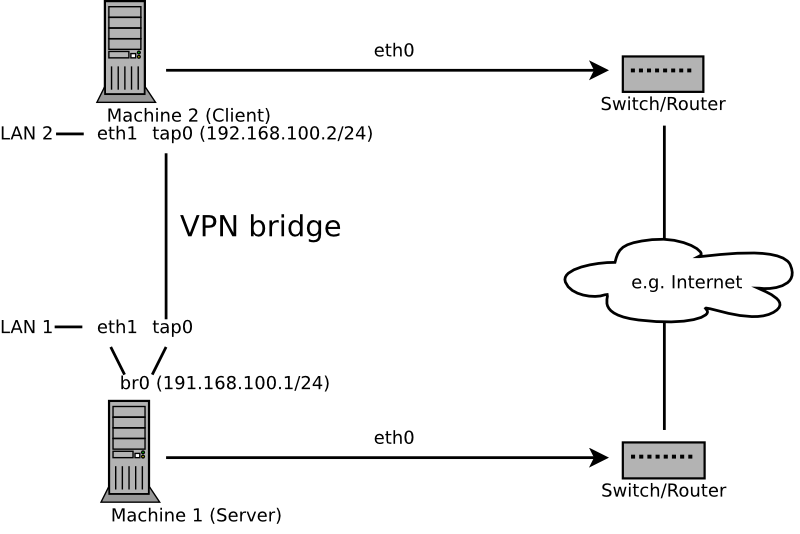
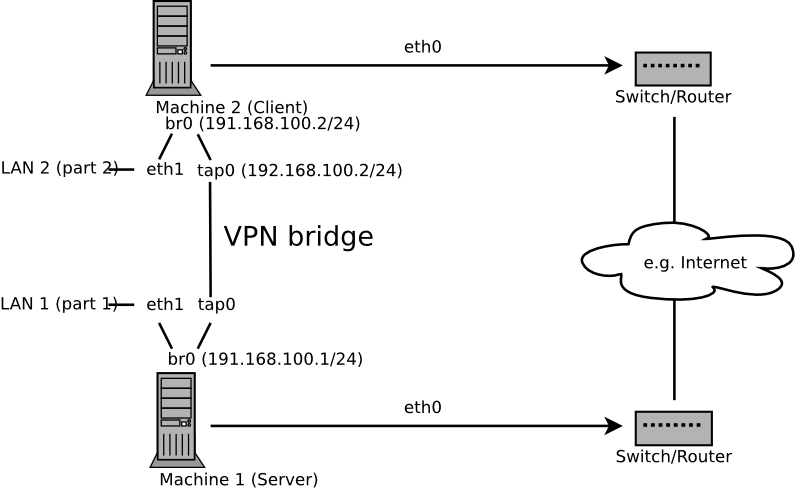
Bridging is a more complex solution. It is recommended when you need to browse Windows file shares across the VPN without setting up a Samba or WINS server. Bridged VPN is also needed if you want to use non-IP protocols (such as IPX) or applications relying on network broadcasts. However, it is less efficient than routed VPN. Another disadvantage is that it does not scale well. This scenarios is depicted in the following figures.
The major difference between bridging and routing is that a routed VPN cannot IP-broadcast while a bridged VPN can.
14.1.3. Tun and Tap Devices¶
Whenever you setup a VPN connection your IP packets are transferred over your secured tunnel. The connection between the client's device and the server's device is called a tunnel. A tunnel can use a so-called tun or tap device. They are virtual network kernel drivers which implement the transmission of ethernet frames or ip frames/packets:
- tun device
A tun device simulates a point-to-point network (layer 3 packets in the OSI model such as Ethernet frames). A tun device is used with routing and works with IP frames.
- tap device
A tap device simulates an ethernet device (layer 2 packets in the OSI model such as IP packets). A tap device is used for creating a network bridge. It works with Ethernet frames.
The userspace program OpenVPN can attach itself to a tun or tap device
to receive packets sent by your OS. The program is also able to write
packets to the device. For more information, see
/usr/src/linux/Documentation/networking/tuntap.txt.
You must install the kernel-source package to read
this file.
14.2. Creating the Simplest VPN Example¶
The following example creates a point-to-point VPN tunnel. It
demonstrates how to create a VPN tunnel between one client and a server.
It is assumed that your VPN server will use private IP addresses like
192.168.1.120 and your client the IP
address 192.168.2.110. You can
modify these private IP addresses to your needs but make sure you select
addresses which do not conflict with other IP addresses.
![[Warning]](admon/warning.png) | Use It Only For Testing |
|---|---|
This scenario is only useful for testing and is considered as an example to get familiar with VPN. Do not use this as a real world scenario to connect as it can compromise your security and the safety of your IT infrastructure! | |
14.2.1. Configuring the VPN Server¶
To configure a VPN server, proceed as follows:
Процедура 14.1. VPN Server Configuration¶
Install the package
openvpnon the machine that will later become your VPN server.Open a shell, become
rootand create the VPN secret key:openvpn --genkey --secret /etc/openvpn/secret.key
Copy the secret key to your client:
scp /etc/openvpn/secret.key root@192.168.2.110:/etc/openvpn/
Create the file
/etc/openvpn/server.confwith the following content:dev tun ifconfig 192.168.1.120 192.168.2.110 secret secret.key
If you use a firewall, start YaST and open UDP port 1194 (++.
Start the OpenVPN service as
root:rcopenvpn start
14.2.2. Configuring the VPN Client¶
To configure the VPN client, do the following:
Процедура 14.2. VPN Client Configuration
Install the package
openvpnon your client VPN machine.Create
/etc/openvpn/client.confwith the following content:remote
IP_OF_SERVERdev tun ifconfig 192.168.2.110 192.168.1.120 secret secret.keyReplace the placeholder
IP_OF_SERVERin the first line with either the domain name, or the public IP address of your server.If you use a firewall, start YaST and open UDP port 1194 as described in Шаг 5 of Процедура 14.1, «VPN Server Configuration».
Start the OpenVPN service as
root:rcopenvpn start
14.2.3. Testing the VPN Example¶
After the OpenVPN is successfully started, test if the tun device is available with the following command:
ifconfig tun0
To verify the VPN connection, use ping on both client and server to see if you can reach each other. Ping server from client:
ping -I tun0 192.168.1.120
Ping client from server:
ping -I tun0 192.168.2.110
14.3. Setting Up Your VPN Server Using Certificate Authority¶
The example shown in Раздел 14.2 is useful for testing, but not for daily work. This section explains how to build a VPN server that allows more than one connection at the same time. This is done with a public key infrastructure (PKI). A PKI consists of a pair of public and private keys for the server and each client and a master certificate authority (CA), which is used to sign every server and client certificate.
The general overview of this process involves the following steps explained in these sections:
14.3.1. Creating Certificates¶
Before a VPN connection gets established, the client must authenticate the server certificate. Conversely, the server must also authenticate the client certificate. This is called mutual authentication.
You can use two methods to create the respective certificates and keys:
Use the YaST CA module (see Глава 15, Managing X.509 Certification), or
Use the scripts included with the
openvpnpackage.
14.3.1.1. Generating Certificates with easy-rsa¶
The easy-rsa utilities use the openssl.cnf file
stored under
/usr/share/openvpn/easy-rsa/.
In most cases you can leave this file as it is.
VER
Процедура 14.3. Generate the Master CA And Key¶
Open a shell and become
root.Change the directory to
/usr/share/openvpn/easy-rsa/. Replace the placeholderVER/VERwith the current version— either1.0or2.0.Copy the file
varsto/etc/openvpnand setexport EASY_RSAto/usr/share/openvpn/easy-rsa:export EASY_RSA="/usr/share/openvpn/easy-rsa/
VER"In the
varsfile change theKEY_COUNTRY,KEY_PROVINCE,KEY_CITY,KEY_ORG, andKEY_EMAILvariables according to your needs.Initialize the PKI:
source /etc/openvpn/vars && ./clean-all && ./build-ca
Enter the data required by the build-ca script. Usually you can take the defaults that you have set in Шаг 4. Additionally set
Organizational Unit NameandCommon Namethat were not set previously.
Once done, the master certificate and key are saved as
/usr/share/openvpn/easy-rsa/.
VER/keys/ca.*
Процедура 14.4. Generate The Private Server Key¶
Change to the
/usr/share/openvpn/easy-rsa/directory.VER/Run the following script:
./build-key-server server
The argument (here:
server) is used for the private key filename.Accept the default parameters, but fill
serverfor theCommon Nameoption.Answer the next two questions («Sign the certificate? [y/n]» and «1 out of 1 certificate requests certified, commit? [y/n]») with
y(yes).
Once done, the private server key is saved as
/usr/share/openvpn/easy-rsa/.
VER/keys/server.*
Процедура 14.5. Generate Certificates and Keys for a Client¶
Change to the
/usr/share/openvpn/easy-rsa/directory. Replace the placeholderVER/VERwith either1.0or2.0.Create the key as in Шаг 2 of Процедура 14.4, «Generate The Private Server Key»:
./build-key client
Repeat the previous step for each client that is allowed to connect to the VPN server. Make sure you use a different name (other than «
client») and an appropriateCommon Name, because this parameter has to be unique for each client.
Once done, the client certificate keys are saved as
/usr/share/openvpn/easy-rsa/keys/client.*
(depending on the name that you have given for the
build-key command).
Процедура 14.6. Final Configuration Steps
Make sure your current working directory is
/usr/share/openvpn/easy-rsa/.VER/Create the Diffie-Hellman parameter:
./build-dh
Create the
/etc/openvpn/ssldirectory.Copy the following files to
/etc/openvpn/ssl:cp keys/ca.{crt,key} keys/dh1024.pem keys/server.{crt,key} /etc/openvpn/sslCopy the client keys to the relevant client machine. You should have the files
client.crtandclient.keyin the/etc/openvpn/ssldirectory.
14.3.2. Configuring the Server¶
The configuration file is mostly a summary of
/usr/share/doc/packages/openvpn/sample-config-files/server.conf
without the comments and with some small changes concerning some paths.
Пример 14.1. VPN Server Configuration File¶
# /etc/openvpn/server.conf port 1194proto udp
dev tun0
# Security
ca ssl/ca.crt cert ssl/server.crt key ssl/server.key dh ssl/dh1024.pem server 192.168.1.120 255.255.255.0
ifconfig-pool-persist /var/run/openvpn/ipp.txt
# Privileges
user nobody group nobody # Other configuration
keepalive 10 120 comp-lzo persist-key persist-tun status /var/log/openvpn-status.log log-append /var/log/openvpn.log verb 4
The TCP/UDP port to which OpenVPN listens. You have to open up the port in the Firewall, see Глава 13, Masquerading and Firewalls. The standard port for VPN is 1194, so in most cases you can leave that as it is. | |
The protocol, either UDP or TCP. | |
The tun or tap device, see Раздел 14.1.3, «Tun and Tap Devices» for the differences. | |
The following lines contain the relative or absolute path to the root
server CA certificate ( | |
Supplies a VPN subnet. The server can be reached by
| |
Records a mapping of clients and its virtual IP address in the given file. Useful when the server goes down and (after the restart) the clients get their previously assigned IP address. | |
For security reasons it is a good idea to run the OpenVPN daemon with
reduced privileges. For this reason the group and user
| |
Several other configurations, see comment in the original
configuration from
|
After this configuration, you can see log messages from your OpenVPN
server under /var/log/openvpn.log. When you have
started it for the first time, it should finish it with:
... Initialization Sequence Completed
If you do not see this message, check the log carefully. Usually OpenVPN gives you some hints what is wrong in your configuration file.
14.3.3. Configuring the Clients¶
The configuration file is mostly a summary from
/usr/share/doc/packages/openvpn/sample-config-files/client.conf
without the comments and with some small changes concerning some paths.
Пример 14.2. VPN Client Configuration File
# /etc/openvpn/client.conf clientdev tun
proto udp
remote
IP_OR_HOSTNAME1194resolv-retry infinite nobind # Privileges
user nobody group nobody # Try to preserve some state across restarts. persist-key persist-tun # Security
ca ssl/ca.crt cert ssl/client.crt key ssl/client.key comp-lzo
We must specify that this machine is a client. | |
The network device. Both clients and server must use the same device. | |
The protocol. Use the same settings as on the server. | |
Replace the placeholder | |
For security reasons it is a good idea to run the OpenVPN daemon with
reduced privileges. For this reason the group and user
| |
Contains the client files. For security reasons, it is better to have a separate file pair for each client. | |
Turns compression on. Use it only when the server has this parameter switched on as well. |
14.4. Changing Nameservers in VPN¶
If you need to change nameservers before or during your VPN session, use netconfig.
Use the following procedure to change a nameserver:
Процедура 14.7. Changing Nameservers¶
Open a shell and log in as
root.Create the file
/etc/openvpn/client.upwith the following contents:/sbin/netconfig modify -i "${1}" -s openvpn <<EOT DNSSEARCH='${domain}' DNSSERVERS='${dns[*]}' EOTStart your VPN connection with rcopenvpn
start.Create the file
/etc/openvpn/client.downwith the following contents:/sbin/netconfig remove -i "${1}" -s openvpnRun netconfig and replace the line
DNSSERVERSwith your respective entry:netconfig modify -i tun0 -s openvpn <<EOT DNSSEARCH='mt-home.net' DNSSERVERS='192.168.1.116' EOT
To check, if the entry has been successfully inserted into
/etc/resolv.conf, execute:grep -v ^# /etc/resolv.conf search mt-home.net mat-home.net nameserver ... nameserver ... nameserver 192.168.1.116
To remove the DNS entry, execute:
netconfig remove -i tun0 -s openvpn
Find another example in
/usr/share/doc/packages/openvpn/contrib/pull-resolv-conf/.
If you need to specify a ranking list of fallback services, use the
NETCONFIG_DNS_RANKING variable in
/etc/sysconfig/network/config. The default value is
auto which resolves to:
+strongswan +openswan +racoon +openvpn -avahi
Preferred service names have the + prefix, fallback
services the - prefix.
14.5. KDE- and GNOME Applets For Clients¶
The following sections describe the setup of OpenVPN connections with the GNOME and KDE desktop tools.
14.5.1. KDE¶
To setup an OpenVPN connection in KDE4 that can be easily turned on or off, proceed as follows:
Make sure you have installed the
NetworkManager-openvpn-kde4package with all dependencies resolved.Right-click on a widget of your panel and select +.
Select .
Right-click on the icon and choose .
Add a new VPN connection with +. A new window opens.
Choose the between or depending on what you have setup with your OpenVPN server.
Insert the necessary files into the respective text fields. From our example configuration these are:
/etc/openvpn/ssl/ca.crt/etc/openvpn/ssl/client1.crt/etc/openvpn/ssl/client1.keyThe user
The password for the user
If you have not used the KDE Wallet System, you are asked if you want to configure it. Follow the steps in the wizard. After you have finished this step, you are reverted back to the dialog.
Finish with .
Enable the connection with your Network manager applet.
14.5.2. GNOME¶
To setup a OpenVPN connection in GNOME that can be easily turned on or off, proceed as follows:
Make sure you have installed the package
NetworkManager-openvpn-gnomeand have resolved all dependencies.Start the Network Connection Editor with Alt+F2 and insert nm-connection-editor into the text field. A new window appears.
Select the tab and click .
Choose the VPN connection type, in this case .
Choose the type. Select between or depending on the setup of your OpenVPN server.
Insert the necessary files into the respective text fields. According to the example configuration, these are:
The user (only available when you have selected )
The password for the user (only available when you have selected )
/etc/openvpn/ssl/client1.crt/etc/openvpn/ssl/ca.crt/etc/openvpn/ssl/client1.keyFinish with and .
Enable the connection with your Network Manager applet.
14.6. For More Information¶
For more information about VPN, visit:
http://www.openvpn.net: Homepage of VPN
/usr/share/doc/packages/openvpn/sample-config-files/: Examples of configuration files for different scenarios/usr/src/linux/Documentation/networking/tuntap.txt, install thekernel-sourcepackage